Displaying items by tag: BTC
ADDED COINPAYMENTS EXCHANGE CRYPTOCURRENCY WALLETS
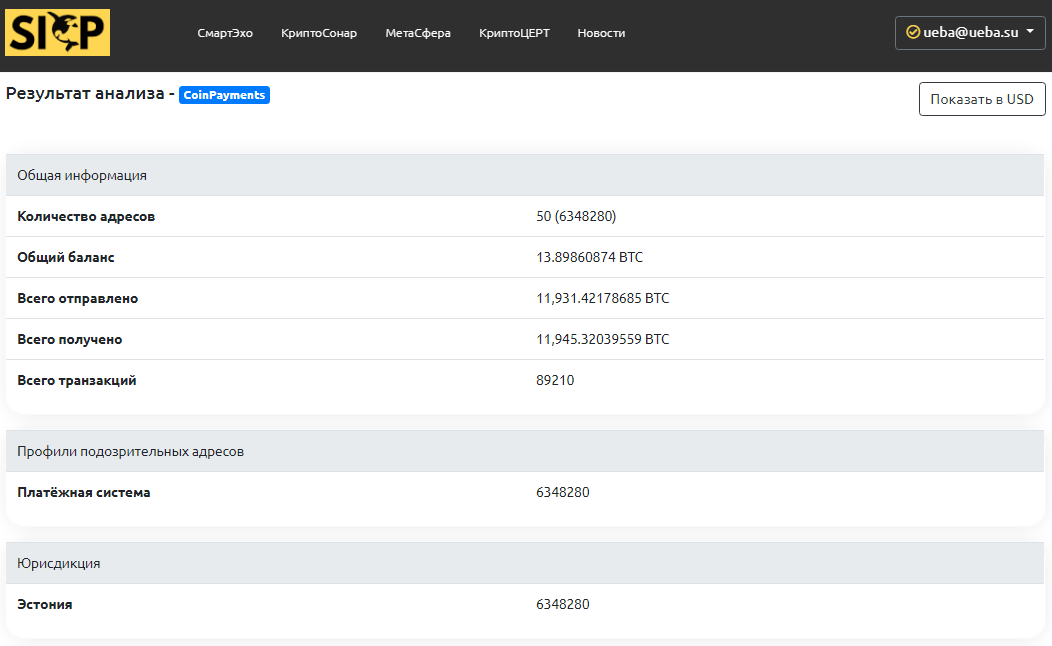
CoinPayments payment system was launched in Estonia in 2013. The electronic wallet of the payment system is used by a large number of sellers and buyers in more than 180 countries, as the wallet supports more than 2005 tokens. The payment system received a regional license to work. However, the withdrawal function to fiat currency is not available.
Over the past 2-3 years, information has been received that cybercriminals have discovered a vulnerability that allows them to withdraw more funds than were in the account. Then the administration of the service compensated for the damage to half of the victims. Also, the site stopped working, which affected a large number of complaints from users and led to problems in investment projects of clients.
CoinPayments also supports the issuance of prepaid cards with a deposit in cryptocurrencies (over 100 types). Such cards can be used in various jurisdictions and carry significant risks of money laundering. There is an official website in the TOR network.
Source: CoinPayments
INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2019
The European Union Agency for Law Enforcement Cooperation, or Europol, 09/10/2019 released its annual Internet Organized Crime Threat Assessment (IOCTA) report for the year. And we weren’t surprised to find that ransomware, despite its palpable decline in volume these past few months—a trend we’ve also seen and documented—remains the most prominent threat in terms of prevalence and financial damage.
While the IOCTA report talks about online threats that both consumers and businesses face on a daily basis, it also puts data at the center of it all. We rely on it—often, all too much—and criminals know this. And yet, most threat actors behind attack campaigns rely on our data to make their attacks more successful, compelling us to take action. After all, nowadays an attack that doesn’t use data against its owners wouldn’t be much of a money-earning scheme.
Threat actors can deprive organizations and individuals’ access to their own files by encrypting and holding them for ransom, such is the case for ransomware. And they can also deny the average user access to an organization’s data (and services) through Distributed Denial of Service (DDoS) attacks. According to Europol, such attacks with an extortion element in them are the most prevalent.
Data also enables other forms of online crime like fraud. Criminals are primarily after financial data, such as credit card information, online banking credentials, and cryptocurrency wallet data. They are also after personally identifiable information (PII) and other login credentials. Such data fuels other profitable, targeted attacks like business email compromise (BEC) scams, spear phishing, and account takeovers.
There is also the challenge of data overload, particularly in the realm of child sexual exploitation (CSE) crimes. The staggering amount of material online detected by law enforcement and private companies continues to increase to the point that it’s putting a strain on law enforcement resources to investigate these crimes. One contributing factor to the increase of availability of CSE material online is that more underage users are accessing and using social media, thus, criminals reach and communicate with them via these platforms.
Other IOCTA findings:
- The IOCTA report also noted that key infection vectors are phishing and remote desktop protocol (RDP) vulnerabilities. Simple patching can address vulnerabilities. As for phishing, did you know that you can be targeted on your desktop and smart phone?
- Organizations are growing more concerned about sabotage performed by malicious insiders.
- Ransomware tactics have shifted, from a scattergun approach of infecting systems to a more focused and refined targeting of profitable victims. This means that ransomware proponents target those with a greater ability to pay a ransom than the average, normal user.
- BEC is evolving. There have been campaigns wherein threat actors used malware and network intrusion.
- Self-generated explicit material (SGEM) is on the uptick. Young children now have access to high-quality smart phones, which enables them to produce and share SGEM, either voluntarily or under coercion. The rising number of SGEM victims will likely to continue. Parents and guardians: Please talk to your kids about this, and other online risks.
- Jackpotting, also known as black-box attacks, against ATMs are becoming more widespread and accessible due to tools like Cutlet Maker being more available on the dark web.
- Card-not-present (CNP) fraud and skimming continue to plague financial institutions. Don’t be a victim of skimming.
- Due to law enforcement activity and extensive DDoS attacks against hidden services, many have grown distrustful of the onion router (Tor) environment. While underground market administrators are currently exploring alternatives, a migration to a new platform will not likely happen yet.
Source: Europol
Source: Malwarebytes Labs
О КОСАтка
Корпоративная система аналитики Транзакция Криптовалюта Актив - кибербезопасность инфраструктуры блокчейнов и антифрод в криптовалютной сфере (антискам, прозрачность, комплаенс).
Связаться
Российская Федерация, Москва
Тел.: +7 (911) 999 9868
Факс:
Почта: cosatca@ueba.su
Сайт: www.ueba.su