Блог
INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2019
Written by Aleksandr PodobnykhThe European Union Agency for Law Enforcement Cooperation, or Europol, 09/10/2019 released its annual Internet Organized Crime Threat Assessment (IOCTA) report for the year. And we weren’t surprised to find that ransomware, despite its palpable decline in volume these past few months—a trend we’ve also seen and documented—remains the most prominent threat in terms of prevalence and financial damage.
While the IOCTA report talks about online threats that both consumers and businesses face on a daily basis, it also puts data at the center of it all. We rely on it—often, all too much—and criminals know this. And yet, most threat actors behind attack campaigns rely on our data to make their attacks more successful, compelling us to take action. After all, nowadays an attack that doesn’t use data against its owners wouldn’t be much of a money-earning scheme.
Threat actors can deprive organizations and individuals’ access to their own files by encrypting and holding them for ransom, such is the case for ransomware. And they can also deny the average user access to an organization’s data (and services) through Distributed Denial of Service (DDoS) attacks. According to Europol, such attacks with an extortion element in them are the most prevalent.
Data also enables other forms of online crime like fraud. Criminals are primarily after financial data, such as credit card information, online banking credentials, and cryptocurrency wallet data. They are also after personally identifiable information (PII) and other login credentials. Such data fuels other profitable, targeted attacks like business email compromise (BEC) scams, spear phishing, and account takeovers.
There is also the challenge of data overload, particularly in the realm of child sexual exploitation (CSE) crimes. The staggering amount of material online detected by law enforcement and private companies continues to increase to the point that it’s putting a strain on law enforcement resources to investigate these crimes. One contributing factor to the increase of availability of CSE material online is that more underage users are accessing and using social media, thus, criminals reach and communicate with them via these platforms.
Other IOCTA findings:
- The IOCTA report also noted that key infection vectors are phishing and remote desktop protocol (RDP) vulnerabilities. Simple patching can address vulnerabilities. As for phishing, did you know that you can be targeted on your desktop and smart phone?
- Organizations are growing more concerned about sabotage performed by malicious insiders.
- Ransomware tactics have shifted, from a scattergun approach of infecting systems to a more focused and refined targeting of profitable victims. This means that ransomware proponents target those with a greater ability to pay a ransom than the average, normal user.
- BEC is evolving. There have been campaigns wherein threat actors used malware and network intrusion.
- Self-generated explicit material (SGEM) is on the uptick. Young children now have access to high-quality smart phones, which enables them to produce and share SGEM, either voluntarily or under coercion. The rising number of SGEM victims will likely to continue. Parents and guardians: Please talk to your kids about this, and other online risks.
- Jackpotting, also known as black-box attacks, against ATMs are becoming more widespread and accessible due to tools like Cutlet Maker being more available on the dark web.
- Card-not-present (CNP) fraud and skimming continue to plague financial institutions. Don’t be a victim of skimming.
- Due to law enforcement activity and extensive DDoS attacks against hidden services, many have grown distrustful of the onion router (Tor) environment. While underground market administrators are currently exploring alternatives, a migration to a new platform will not likely happen yet.
Source: Europol
Source: Malwarebytes Labs
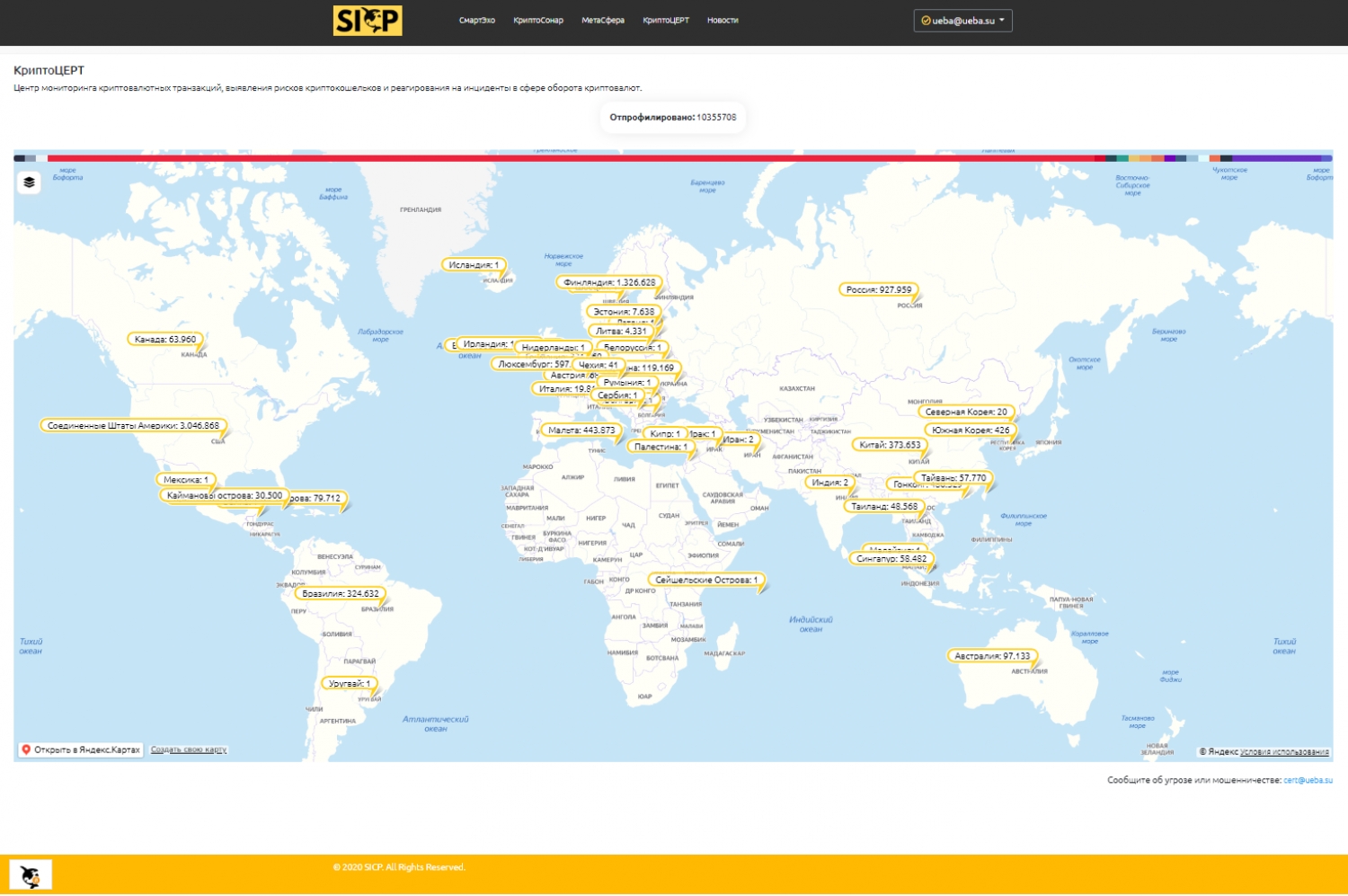
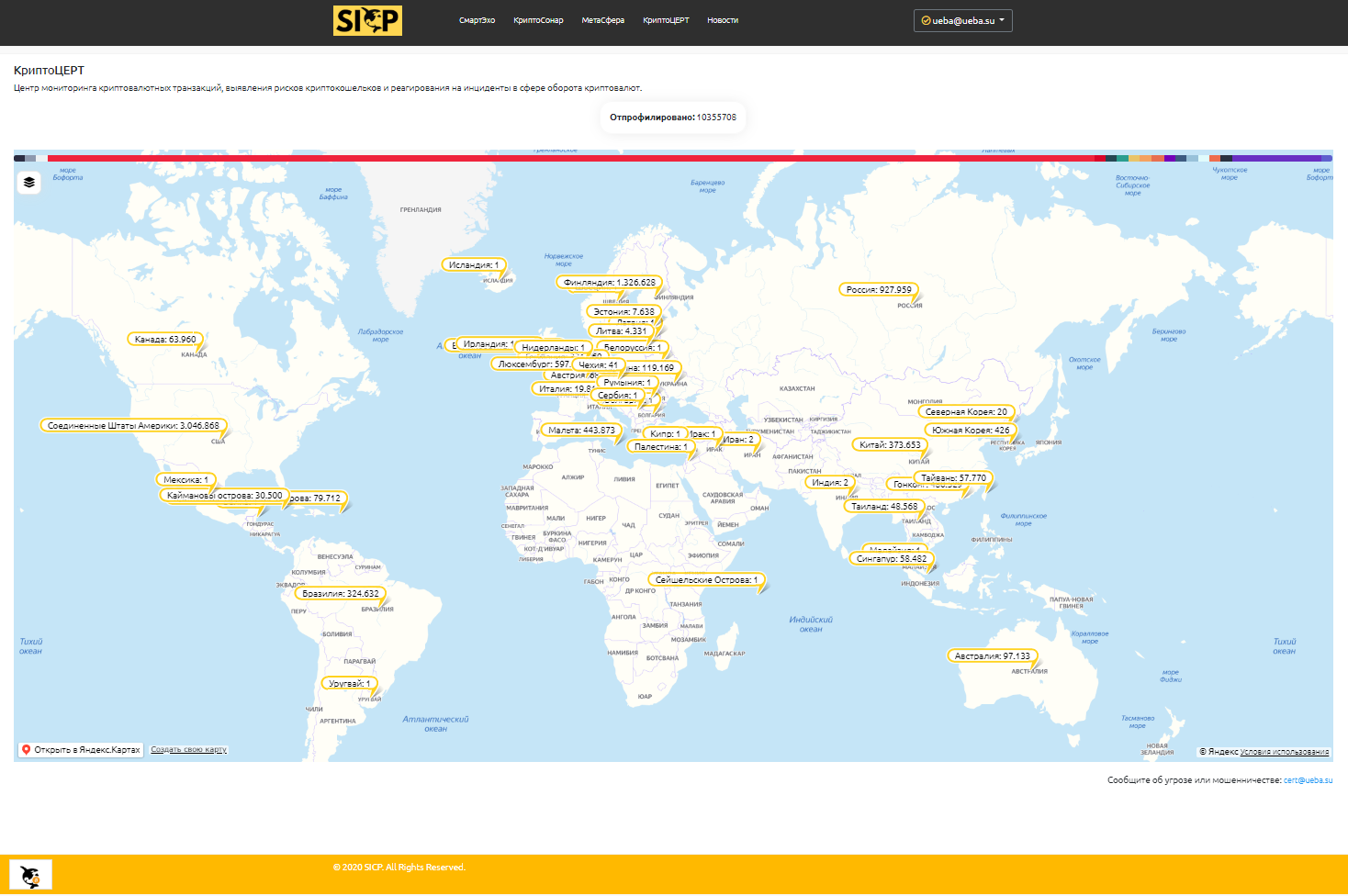
On July 30, the SICP (Security Intelligence Cryptocurrencies Platform) platform announced the launch of the first Russian commercial Center for monitoring cryptocurrency transactions, identifying the risks of cryptocurrency wallets and responding to incidents in the field of cryptocurrency circulation (CryptoCERT).
This service is the first in Russia and the UIS. Today, any citizen or organization can send information about fraud (another threat or risk) related to cryptocurrencies. Additionally, the publicly available interactive map displays profiled crypto wallets by country. The custom menu allows you to display one or more profiles. The legend displays the share and number of wallets associated with the profile. For registered and verified users, a wider visualization functionality is available.
It should be noted that on July 22, the State Duma of the Russian Federation adopted in the 3rd reading the law "On digital financial assets". The new rules will enter into force on January 1, 2021. The law "On digital currency" is expected to be considered in the coming autumn.
Remarkably, today is World Day Against Trafficking in Persons. It is a serious crime and gross violation of human rights. The United Nations Office on Drugs and Crime (UNODC), as the guarantor of the United Nations Convention against Transnational Organized Crime and the Protocols thereto, assists States in their efforts to implement the Trafficking in Persons Protocol.
By the way, this factor is taken into account when assessing the risks of crypto wallets, in the SmartEcho service, and identifying suspicious transactions ...
Source: sicp.ueba.su
Source: k4y0t.ru
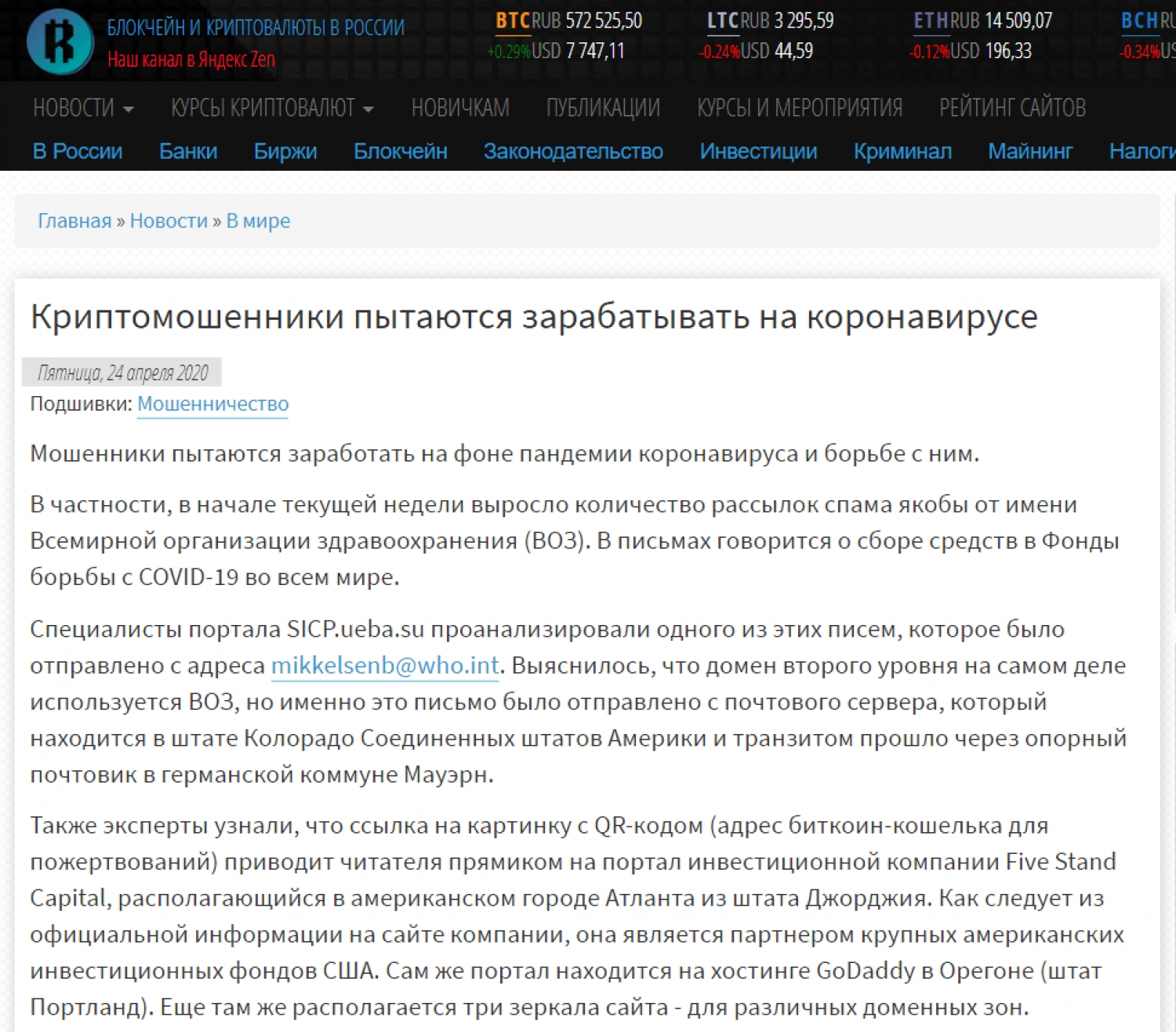
CRYPTO SCAMMERS ARE TRYING TO MAKE MONEY ON THE CORONAVIRUS
Written by Dobryshkin SergeyFraudsters are trying to make money amid the coronavirus pandemic and the fight against it. In particular, at the beginning of this week the number of spam mails allegedly on behalf of the World Health Organization (WHO) has increased. The letters speak of fundraising for COVID-19 Funds worldwide.
Specialists of the portal SICP.ueba.su analyzed one of these letters, which was sent from This email address is being protected from spambots. You need JavaScript enabled to view it.. It turned out that the second-level domain is actually used by WHO, but it was this letter that was sent from a mail server located in the state of Colorado in the United States of America and in transit passed through a reference mailer in the German municipality of Mauern.
Experts also learned that a link to a picture with a QR code (the address of a bitcoin wallet for donations) leads the reader directly to the portal of the investment company Five Stand Capital, located in the US city of Atlanta from Georgia. As follows from the official information on the company's website, it is a partner of large US investment funds in the United States. The portal itself is hosted by GoDaddy in Oregon (Portland). Still there are three site mirrors - for various domain zones.
This email was first sent from the SendGrid.net mail server, which is also located on GoDaddy’s resources in Colorado, Denver. And, judging by the information bases, another 13 resources are located on this IP address, nevertheless, only one of them is displayed - a web-based mail gateway.
It is important to consider that on the official website of the WHO there is no way to donate funds in the form of cryptocurrency - bitcoin. The same is true of their dedicated donation collection site. And there is even a warning that they do not send any letters.
Apparently, fraudsters are trying to cunningly take advantage of the global crisis situation, possessing a good knowledge of modern technology. Or maybe the owners of WHO decided to use all available tools to raise funds. And experts are wondering, where is the hosting site for WHO?
Interestingly, so far, no funds have been received to the cryptocurrency wallet, which is indicated in the letter of the scammers. The wallet is constantly monitored by SICP platform experts, however, like other malicious purses known to them.
Source: CryptoRussia.ru
EXPERIMENTAL LEGAL REGIME FOR AI IN MOSCOW (BRIEF REVIEW OF THE LAW)
Written by Manuylova NatalyaOn April 24, 2020, Russian President Vladimir Putin signed the Law “On an experiment to establish special regulation in order to create the necessary conditions for the development and implementation of artificial intelligence technologies in the subject of the Russian Federation - the city of federal significance Moscow and amending Articles 6 and 10 of the Federal Law” About personal data.
Essentially brief:
- from July 1, 2020, over 5 years, an experiment will be conducted in Moscow to establish special regulation in order to create the necessary conditions for the development and implementation of artificial intelligence technologies in Moscow, as well as the subsequent possible use of the results of the application of artificial intelligence in other regions. At the end of the term, regulatory documents issued for the purpose of the experiment are canceled;
- in the Law for the realization of its goals the concept of “artificial intelligence”, as well as “artificial intelligence technology” is given;
- in order to establish an experimental legal regime (hereinafter referred to as the ELR), the Moscow Government will determine, inter alia, cases of mandatory application and (or) consideration of the results of the use of artificial intelligence in the activities of the Moscow Government, as well as the procedure and cases of transfer by owners of funds and photo and video surveillance of images obtained in accordance with the conditions provided for in subparagraphs 1 and 2 of paragraph 1 of Article 1521 of the Civil Code of the Russian Federation, as well as providing access to such media cameras and photo and video surveillance systems to state authorities and organizations performing public functions in accordance with regulatory legal acts of the Russian Federation. The list of organizations performing public functions is established by the Moscow Government;
- when making transactions and other legally significant actions, an ELR participant will be obliged to notify persons who are not participants in the experimental legal regime of his status as an ELR participant and indicate the application of the Moscow Government adopted in accordance with the Law in relation to his regulatory acts. if the legally significant actions specified in this part are committed using the Internet information and telecommunication network, the participant in the experimental legal regime inform the user (party to the transaction) of all applicable provisions of regulatory legal acts of the Government of Moscow adopted in accordance with the Law in question
- requirements for agreements between ELR participants and the authorized body (it is appointed by the Moscow Government), should provide mechanisms to ensure the confidentiality of the transmitted data and the security of their storage.
- (!) Personal data obtained as a result of depersonalization and processed in accordance with paragraph 6 of part 1 of Article 4 of the relevant Law cannot be transferred to persons who are not parties to the ELR. In the event that the ELR participant status is lost or the experiment is terminated after its expiration, the person who is the ELR participant loses the right to receive personal data obtained as a result of depersonalization and personal data stored in the form The result of such depersonalization is subject to destruction in the manner established by the authorized body by agreement with the authorized federal executive body, carrying out functions for the development and implementation of state policy and regulatory regulation in the field of information technology.
- for the destruction of personal data obtained as a result of depersonalization, in the prescribed manner, the procedure for assessing the conformity of information protection means, which include the function of information destruction, is carried out. The participants of the ELR are responsible for observing the rights of the subjects of personal data in accordance with the Federal Law of July 27, 2006 No. 152-FZ “On Personal Data” for the entire duration of the experiment and after the termination of their participation in the experiment.
- during the experiment, it is not allowed to store personal data obtained as a result of depersonalization and processed on the basis of an agreement with the authorized body specified in paragraph 6 of part 1 of this article, outside the subject of the Russian Federation - the city of federal significance of Moscow.
- the status of an ELR participant is acquired from the moment it is included in the corresponding public register;
- the decision on inclusion or rejection is made by the authorized body (appointed by the Moscow Government) within a period of not more than thirty calendar days from the date of receipt of the application;
- The law provides requirements for the applicant, which, which can only be a legal entity or individual entrepreneur, registered in the territory of Moscow, as well as for the type of activity. The IP and the governing bodies of a legal entity have a requirement for the absence of an unexpunged or outstanding criminal record for crimes in the economic sphere, as well as for crimes of medium gravity, serious and especially serious crimes.
- the reasons for the refusal to be included in the register are prescribed in the Law (it seems to me quite common); in case of refusal to include in the register of ELR participants, the authorized body shall notify the applicant of this with a motivated justification for such a refusal.
- the reasons for the exclusion of the ELR participant from the register are also indicated, the exclusion is carried out within 10 working days.
- the formation of strategic directions and monitoring the activities of participants is planned to be entrusted to the ELR Coordination Council, which, on the proposal of the Government of the Russian Federation, includes representatives of federal executive bodies.
- Amendments to Article 6 and Article 10 of the Federal Law of 07.27.2006 No. 152-FZ "On Personal Data" in terms of processing conditions and in the processing of special personal data, respectively.
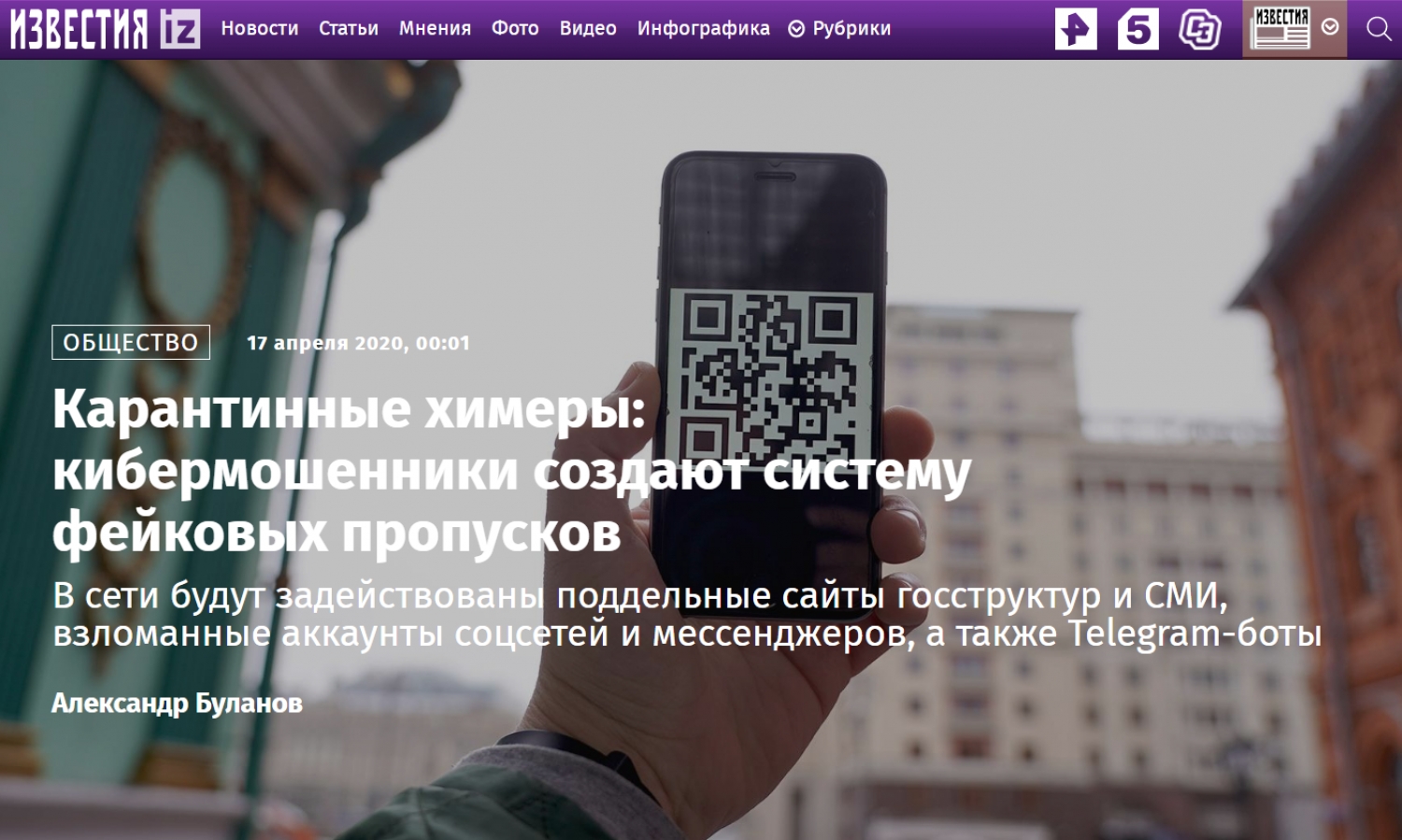
QUARANTINE CHIMERAS: CYBER FRAUDSTERS CREATE A SYSTEM OF FAKE PASSES
Written by Bederov IgorUsing the new scheme, fraudsters plan to steal money and passport data, gain access to accounts on social networks and electronic mailboxes of Russians who needed to issue passes during the quarantine period. At the moment, criminals are working on creating clones of government agencies responsible for issuing documents (including mos.ru, mosreg.ru and gosuslugi.ru), and fake media portals on which it is planned to post fake news, experts told Izvestia on cybersecurity. In addition, the planned hackers and the mass mailing of messages via e-mail, social networks and instant messengers. To protect against intruders, experts advise using information verification services. About how to do this - in the material of Izvestia.
Clone attack
Forced isolation due to the COVID-19 pandemic is forcing people to spend more and more time on the Internet. The network is needed for working remotely, studying, ordering goods and organizing home leisure activities. The growth of traffic was even confirmed by the deputy head of the Ministry of Communications Alexey Volin, who said that "when they stayed at home, the people rushed to the Internet, and rushed there with terrible force."
According to the Russian company "Internet Rozysk", network scammers also decided to take advantage of the trend. Now they are organizing a global criminal system consisting of fake sites, hacked accounts on social networks and malicious Telegram bots. Criminals are going to attract people with a service to provide passes for moving around the city in the context of the COVID-19 epidemic, and then steal their money and personal data.
“We got information about the upcoming action using our bots, which are embedded in the darknet (the shadow segment of the Internet. - Izvestia) and a number of closed chats,” said Igor Bederov, CEO of the company. “We learned from them that a scheme is being prepared for deceiving people who plan to obtain passes for themselves.”
According to the expert, this scheme, known as the “rabbit hole”, involves the mass mailing of addresses of fake sites that will be as similar as possible to the resources of government agencies with the authority to issue documents (including mos.ru, mosreg.ru and gosuslugi.ru ) It is expected that this will happen with the help of hacked accounts on social networks and Telegram bots. Attackers will try to confirm the legitimacy of the messages with links to articles allegedly posted in leading Russian media - their sites will also receive clones.
Throughput pressure
After users switch to malicious resources, they will be asked for passport data for issuing passes, as well as bank card details - supposedly to pay for the service upon receipt.
“Their further actions can be predicted from earlier criminal actions of this type, which, in particular, were conducted under the guise of receiving certain compensatory state payments or paid bank surveys,” warned Igor Bederov. - Then the criminals, as a rule, sought a voluntary transfer of money, after which they managed to withdraw the remaining funds from the cards with the help of the details already received.
At the same time, personal data of users is likely to become goods for sale on the black market, forming new illegal bases. The final stage of the scheme is usually the hacking of the personal accounts of the deceived user on social networks and his mailboxes (this is done using the captured cookies), after which they are connected to the distribution of malicious messages.
The large-scale nature of the illegal action was confirmed by specialists of the Security Intelligence Cryptocurrencies Platform (SICP) risk analysis service.
“The scale of the new threat is comparable to the financial pyramids, the organizers of which spend huge sums on promotion through famous people and popular sites,” said Aleksandr Podobnykh, an independent expert at SICP. - And the state’s symmetric response to this, I’m afraid, can only be a significant increase in control over SIM cards, hosting and data centers.
According to experts, in addition to the already mentioned increase in Russian Internet traffic, there are a number of additional factors that will play into the hands of criminals, increasing their chances of success.
“First of all, they include neurotization of people against the background of the epidemic, which makes it easier to manipulate,” said Luka Safonov, director of the information security department of the National Engineering Corporation. - On the other hand, the situation is complicated by the situation with state portals, which now do not withstand the influx of visitors. The fact is that when people cannot get a pass through an official resource, they are most likely to be interested in an alternative offer.
Simple calculations
Despite the sophistication of criminal methods, you can still protect yourself from fraud using a few simple tools that allow you to calculate fraudsters. The instruction for checking incoming messages to Izvestia was provided by Internet Rozysk:
- all state organizations and private companies operating in Russia have domain names registered in our country. Therefore, suspicious links should be checked through the WHOIS service, which reveals their true owners. If, according to the results of the examination, they turn out to be hidden, then it is better not to trust the received information.
- checking the sender of the letter, which can be carried out through the verifiers of mailboxes located on the sites https://2ip.ru/mail-checker/, will be useful in such a situation; http://ru.smart-ip.net/check-email/ and https://ivit.pro/services/email-valid/. It will make sure that the message came from the server of the organization whose employees were indicated as its authors.
- also an indirect sign of fraud can be the so-called shortened link, which has the end click.ru, goo-gl.ru, etc. Its original address is also worth checking (without going to it!) Using special services - they are available at: https://scanurl.net/; https://vms.drweb.ru/online/, https://virusdesk.kaspersky.ru/ and https://iplogger.ru/url-checker/.
The Izvestia source in the power structure confirmed the need for additional verification of the legitimacy of the request when receiving a request for the transfer of funds. “This needs to be done even if it seems that the message was sent to one of the state structures,” he noted.
The expert also proposed an additional way to check emails received via e-mail: you should try to reply to a suspicious message. If the address of the organization’s employee does not change, then with a high degree of probability it is not fake.
However, this does not eliminate the need for additional checks described in the instructions.
Roskomnadzor responded to a request from Izvestia that they were ready to promptly send administrators of sites hosting false information notifications of the need to delete it, if the Prosecutor General's Office so requires.
“If this instruction is not followed, information will be communicated to telecom operators about the need to limit the access of Russian users to this content,” the organization noted.
At the same time, Roskomnadzor emphasized that they do not have the authority to conduct investigations to prevent cybercrime and fraud on the Internet.
Izvestia also sent inquiries to the Ministry of Internal Affairs, the FSS and the Moscow Department of Information Technology. However, operational responses could not be obtained.
Source: IZ.ru
Expert Natalia Manuylova invites to a video conference DI Digital Identity to discuss the topic of digital identification, a number of FATF documents. This is a test meeting. Only important points will be affected, without “water procedures”. Welcome! The number of free tickets is limited ...
At the online event, scheduled for April 23 (from 11:30 to 12:30), you can get answers to questions such as: What are some common examples of digital identification? Why does the FATF pay special attention to ID? FATF document overview. Lawyers, AML / CFT specialists and other interested parties are invited to participate.
Source: TimePad.ru
SICP PASSED STATE REGISTRATION IN THE FEDERAL SERVICE FOR INTELLECTUAL PROPERTY OF THE RUSSIAN FEDERATION
Written by Aleksandr PodobnykhThe quarantine situation causes the rapid development of distance services, as well as the widespread use of contactless payments and electronic currencies. At the same time, a significant event took place on the Russian cryptocurrency market. A few days ago, the SICP platform team received a notification from the Federal Intellectual Property Service of the Russian Federation about the state registration of a computer program (03/18/2020 No. 2020613600) - Security Intelligence Cryptocurrency Platform (SICP) or Cognitive (corporate) analytics system Transaction Cryptocurrency Asset.
The platform’s web services are designed to provide cybersecurity for the infrastructure of blockchains (distributed registries) and implement anti-fraud measures in the field of cryptocurrency circulation. Functionality: risk assessment of Digital Assets; cryptocurrency investigations; conducting complex events in the field of cryptocurrency circulation; cryptocurrency wallet and ICO reliability assessment; tracking transactions correlating with a real object (organization); ordering advice on the possibility of an investigation (and the collection of necessary evidence); Advanced analytics of public blockchains and reports on suspicious transactions and related objects.
Today, a large number of SICP users leave user ratings about crypto-wallets and transactions, researchers actively use the SmartEcho and CryptoSonar services to evaluate crypto-wallets and visualize research (investigation) scenes, experts use CryptoSonar and MetaSphere services to save scenes and analyze the wallet and transaction pool (by internal tags).
In your personal account, verification tools are available for owners of crypto-wallets and even crypto-firms, with obtaining the appropriate status (and the ability to share certificates on social networks and on sites). There is the possibility of monitoring wallets for incoming / outgoing transactions (other events), saved scenes and functionality for conducting joint investigations (by registered users).
It is noteworthy that it is on Cosmonautics Day that we will announce this event! .. A significant step, if not for the entire global financial and technological sector, then surely for the entire industry of end-to-end technologies...
Source: K4Y0T Project.
LAWYER APPRECIATED THE PLANS OF CENTRAL BANK TO CHANGE THE GROUNDS FOR BLOCKING ACCOUNTS
Written by Manuylova NatalyaNatalya Manuylova, a forensic expert and teacher at the Moscow Digital School, commented on the Bank of Russia’s plans at the request of Izvestia to clarify the signs that could cause banks to consider their clients' actions suspicious.
The list of reasons for blocking an account has not been changed since they appeared in March 2012. Earlier, on February 17, it became known that the Central Bank proposes not only to introduce new criteria, but also to exclude some of the more than 100 existing ones, according to which banks recognize transactions as doubtful.
“The Bank of Russia revised the list of unusual transactions, excluding a number of signs, and added new signs taking into account the realities of the financial market. It is worth noting that the list of unusual operations only orient banks to pay special attention to operations that have signs of unusual. Unfortunately, quite often confused are signs of dubious operations and operations that have signs of unusual ones”, the expert added.
Regarding the qualifications of operations with digital and virtual assets, much will depend on the qualifications of bank employees, Natalya Manuylova added.
According to her, if bank employees do not have enough qualifications, then Rosfinmonitoring will replenish with information about operations that are not related to dubious ones.
Moreover, the market will resume pressure on the business to provide documents not related to the operation, threats to block customer accounts, delays in operations.
“For example, the symptom in section 11,“ The transaction is related to the acquisition or sale of virtual assets ”should be adapted for banks in the existing risk management system. The Bank should develop its own additional criteria for qualifying such an operation as “doubtful,” for example, the amount of the transaction, the business reputation of the counterparty, the counterparty’s bank, and so on. Considering that a number of signs are quite common, I think that the Bank of Russia is waiting for a rather large number of requests from both banks and customers, but here it’s already in the form of complaints, ”concluded the forensic expert.
In February, Russian Prime Minister Mikhail Mishustin, during a meeting with the head of Sberbank German Gref, said that the bank’s technologies and services would be used to simplify the life of Russians and to create a state-owned digital platform.
Source: IZ.ru
More...
The world is divided into parts regarding the cryptocurrency environment. Some advocate a ban on digital currency, others offer only some restrictions, and some states impose a complete ban on cryptocurrencies. The motivation for the ban and restrictions on cryptocurrency is the fight against crime and money laundering.
So the State of Qatar has added to the list of countries with a ban on the circulation of cryptocurrency. A statement by the Qatar Financial Center regulator states that "Virtual Asset Services cannot be held in or out of QFC at this time." It stated that the ban included “anything valuable that replaces a currency, can be sold or digitized and can be used for payment or investment”.
Simplecoin, a Netherlands-based cryptocurrency 'mining pool' set up to enable collaborative discovery of new virtual currency coins, and Chopcoin, a Bitcoin gaming platform, announced they would be shutting down before the EU Fifth Anti-Money Laundering Directive (5AMLD), came into effect in all EU Member States on 10 January 2020.
The 5AMLD requires providers of crypto platforms and wallets to identify their customers for anti-money laundering purposes.

Source: Intelligence for the Global Adviser and Wealth Manager.
RUSSIAN FEDERATION'S MEASURES TO COMBAT MONEY LAUNDERING AND TERRORIST FINANCING
Written by Aleksandr PodobnykhParis, 17 December 2019 - The Russian Federation (Russia) has an in-depth understanding of its money laundering and terrorist financing risks and has established policies and laws to address these risks, but it should enhance its approach to supervision and prioritise the investigation and prosecution of complex money laundering cases, especially concerning money being laundered abroad.
The Financial Action Task Force (FATF), the Eurasian Group and MONEYVAL, assessed Russia’s anti-money laundering and counter terrorist financing (AML/CFT) system. The assessment is a comprehensive review of the effectiveness of Russia’s measures and their compliance with the FATF Recommendations. This includes an assessment of its actions to address the risks emanating from UN and domestically designated terrorists and terrorist organisations. The report does not address the justification that led to the domestic designation of an entity as a terrorist or terrorist group or organisation.
Russia recognises that it faces significant money laundering risks as a result of the proceeds of crimes committed within the country, in particular those related to corruption and its role as both a transit and destination country for narcotics trafficking. A national risk assessment, complemented by in-depth knowledge of relevant law enforcement agencies, has allowed the country to identify and understand its risks, including terrorist financing risks. Russia’s legal framework appropriately addresses these risks and the country has formal policies in place, supported by strong domestic co-ordination and co-operation, to combat money laundering and terrorist financing. However, the country needs to address gaps in its ability to freeze, without delay, assets linked to terrorism, financing of terrorism and proliferation of weapons of mass destruction, and ensure that this freezing obligation extends to all natural and legal persons.
In general, Russia cooperates with foreign counterparts, including through more than 100 international co-operation agreements with its financial intelligence unit, Rosfmonitoring. Authorities make excellent use of financial intelligence, based on a wealth of collected data and analysed with sophisticated technologies to contribute to money laundering and terrorist financing investigations. While the country has prioritised getting money back for the victims of crimes – around EUR 816 million per year – it needs to focus more on the investigation and prosecution of complex money laundering cases, especially concerning money being laundered abroad.
Russia has strengthened its oversight of the banking sector and has now mitigated the risks of criminals being the owners or controllers of financial institutions. However, deficiencies in licensing remain and the sanctions for banks that do not comply with AML/CFT requirements are not effective or dissuasive.
In general, financial and certain non-financial entities such as accountants and auditors, have a good understanding of how their services could be used to launder the proceeds of criminal activity or terrorist financing, but given that Russia is a significant centre for mining precious metals and stones, this sector’s understanding of risk is not in line with the country’s risk assessment.
Since its last assessment in 2008, Russia has strengthened its understanding of the money laundering and terrorist financing risks it faces and has developed a robust legal framework to address them. The country has taken a number of actions that have delivered concrete results. But, the country needs to address the areas of weakness this report has identified.

The FATF adopted this report at its October 2019 Plenary meeting.
OPERATORS OF INVESTMENT PLATFORMS ARE OBLIGED TO ORGANIZE MEASURES TO AML/CFT
Written by Manuylova NatalyaFrom 01.01.2020, a new entity will appear on the financial market - the operator of the investment platform. In accordance with subparagraph 7) of clause 1 of article 2 of Federal law dated 02.08.2019 No. 259-FL "On attracting investments using investment platforms and on amending certain legislative acts of the Russian Federation" the operator of the investment platform is a business company created in accordance with the legislation of the Russian Federation, carrying out activities to organize investment attraction and included by the Bank of Russia in the register of investment platform operators.
It is worth noting that from 01.01.2020 the amendments to the Federal Law of 07.08.2001 also come into force. No. 115-FL "On combating the legalization (laundering) of proceeds from crime and the financing of terrorism" (hereinafter - Law No. 115-FL), according to which:
1. Operators of investment platforms become the subject of Law No. 115-FL (Supplement to the first part of Article 5 with a new fourth paragraph of the above law);
2. The operators of investment platforms are entrusted with the obligations specified in Article 7 of Law No. 115-FL, including the application of measures to freeze (block) money or other property in accordance with the requirements established by subparagraph 6 of paragraph 1 of Article 7 of Law No. 115- Federal Law.
3. The operators of investment platforms have been granted the rights specified in Article 7 of Law No. 115-FL, in particular:
- simplified identification of investment platform operators with respect to customers in certain cases, namely: when concluding agreements on the provision of investment assistance services involving investment using the investment platform for an amount not exceeding 100,000 rubles, provided that all settlements are carried out exclusively in non-cash form on accounts opened with a Russian credit institution;
- an assignment of the identification procedure to third parties - on the basis of the contract to entrust the credit organization with the identification or simplified identification of the individual customer, as well as the identification of the client’s representative, beneficiary and beneficial owner.
4. The internal control rules of the Investment Platform Operators are developed taking into account the requirements approved by the Central Bank of the Russian Federation in agreement with the authorized body, and approved by the head of the organization.
5. Qualification requirements for special officials responsible for the implementation of internal control rules, targeted internal control rules, as well as requirements for training and education, identification of clients, client representatives (including identification of the sole executive body as a representative of the client), beneficiaries and beneficial owners are determined in accordance with the procedure established by the Bank of Russia.
Please note that non-compliance with the requirements of Law No. 115-FL entails the prosecution of an official and organization on the basis of Article 15.27 of the Code of Administrative Offenses of the Russian Federation. The consequences of non-compliance with the requirements of the AML/CFT legislation May result in criminal prosecution.
For questions regarding the organization of work on the implementation of Law No. 115-FL and training, write to This email address is being protected from spambots. You need JavaScript enabled to view it. or This email address is being protected from spambots. You need JavaScript enabled to view it..
THE ROUNDTABLE PARTICIPANTS LEARNED ABOUT THE FEATURES OF SMART CONTRACTS
Written by Manuylova NatalyaOn November 5, 2019, a round table was held at the Moscow Chamber of Commerce and Industry on the topic: “Electronic Commerce. Smart contracts. New Opportunities of the Digital Economy ”, which discussed the main problems of legal support of electronic commerce.
At the event, the main trends of the digital economy were presented and the state of legal regulation of this sphere was outlined. According to Suren Vardanyan, Vice President of the Chamber of Commerce and Industry, opening the meeting, the Chamber pays special attention to digitalization issues: digital products are being developed that allow entrepreneurs to receive new services, and the Chamber follows the main economic trends. “We try at all the events that take place within the walls of the MCCI to develop specific proposals, which we then pass on to the authorities and all interested departments,” Vardanyan emphasized.
According to Igor Sudets, Deputy Director of the Digital State Development Department of the Ministry of Digital Development, Telecommunications and Mass Media of the Russian Federation, 17 draft laws are currently being drafted to regulate the main directions of digitalization of the Russian economy. In the near future it is expected that the Government will give instructions on the preparation of about 60 more draft laws. For example, the draft law on digital financial assets has already undergone seven editions, but has not yet been submitted to the State Duma. Now the eighth version of the document is being prepared. The total budget allocation for federal projects related to the implementation of digital technologies is 1634.9 billion rubles. The main national programs being implemented now, according to Igor Sudets, are a training program for the digital economy; digital infrastructure creation; digital technology development; digital security; development of legal regulation and the creation of digital state regulation. As for the latter, as stated by the representative of the Ministry of Communications, the basic principle of digital government is “a person does not need to know which authority he interacts with. He sends a request, and the state executes it. " Moreover, according to the expert, “the state itself should come to us”: after some time, every citizen can receive push notifications about what actions he needs to take: pay taxes, replace a driver’s license, etc.
Artem Dalevich, Vice President of the ICIE, spoke about the implementation of the secure transaction mechanism using escrow accounts on the Business Market platform, developed and implemented by the MCCI
Since lawyers made up a large share of the roundtable audience, one of the main topics of discussion was the legal regulation of electronic commerce. Senior Associate at Rödl & Partner Alexandra Nechaeva spoke about the main risks that accompany the conclusion of contracts in online trading. It was, in particular, about the interpretation of the concept of an offer and the moment of its receipt, as well as about the differences between online and distance trading. The speaker emphasized that there is no definition of electronic commerce in the legislative field, which leads to a rather arbitrary interpretation of the electronic commerce process in judicial practice. In addition, Alexandra Nechaeva said that Russia has not developed approaches to determining the jurisdiction of transactions involving foreign elements. Summing up her speech, the speaker noted that “the problems of determining jurisdiction are now one of the first in matters of the digital economy”.
Svetlana Mochalina, head of the risk management department at L'Occitane, spoke about the legal risks of an international company in the retail industry in Russia. A franchise firm defended its interests by registering trademark rights. This almost completely prevented parallel sales.
The topic of the speech of DDC Ltd Director Ilya Mikheev was smart contracts. Since this is a very promising form of digital agreements, the message caused serious interest from the audience. According to the expert, for the first time a smart contract appeared a long time ago - in 1996. “In principle, a smart contract is a computer code that guarantees the fulfillment of obligations subject to all agreed conditions,” the speaker explained. Another important distinguishing feature of a smart contract is that it must be hosted in a decentralized, trusted environment. Such an environment is guaranteed, in particular, by blockchain technology. Smart contracts are already used, for example, in diamond verification.
The representative of the company-operator of fiscal data OFD.ru Dmitry Pogozhev talked about the currently introduced product labeling system, its advantages and disadvantages.
Summing up the round table, the moderator of the meeting, forensic financial expert Natalya Manuylova noted that "the digital economy is not only cryptocurrency and blockchain." The main purpose of the event was to identify the risks that entrepreneurs face in introducing digital technologies, and to outline ways to minimize them, including using compliance procedures.
The Advisor to the President of the MCCI Marina Evteeva thanked all the speakers and participants for the informative conversation and assured that all the proposals that were voiced would be summarized and brought to the attention of the leadership of the chamber.
The event was supported by the Government of Moscow and the Department of Economic Policy and Development of Moscow...
Search
Blog Category
Popular Post
Latest News
О КОСАтка
Корпоративная система аналитики Транзакция Криптовалюта Актив - кибербезопасность инфраструктуры блокчейнов и антифрод в криптовалютной сфере (антискам, прозрачность, комплаенс).
Связаться
Российская Федерация, Москва
Тел.: +7 (911) 999 9868
Факс:
Почта: cosatca@ueba.su
Сайт: www.ueba.su